Data Platform Security
In today's data-driven enterprise landscape, managing who can access what resources has become one of the most critical challenges organizations face. As data platforms grow in complexity and user bases expand, the need for robust, scalable, and flexible access control mechanisms becomes paramount. Traditional authorization systems often struggle with the dynamic nature of modern data platforms, leading to either overly restrictive environments that hinder productivity or overly permissive ones that pose security risks.
Resource Access Management (RAS) represents a sophisticated approach to authorization that addresses these challenges through intelligent resource grouping, fine-grained permission controls, and extensible architecture. At its core, RAS moves beyond simple role-based access control to provide context-aware authorization decisions that consider not just who is making the request, but what they're trying to access, how they're trying to access it, and under what circumstances.
The Challenge of Modern Data Platform Authorization
Modern data platforms like IOMETE encompass a diverse ecosystem of resources: compute instances that process data, Spark jobs that execute analytics workflows, secrets that store sensitive configuration data, worksheets for collaborative analysis, and countless other assets. Each of these resource types has unique characteristics, usage patterns, and security requirements.
Traditional authorization approaches often fall short because they:
- Lack flexibility: Hard-coded permission models that can't adapt to new resource types
- Create silos: Different authorization mechanisms for different services, leading to inconsistent security policies
- Scale poorly: Authorization decisions that become bottlenecks as user and resource counts grow
- Provide limited visibility: Difficulty in understanding and auditing who has access to what
The result is often a patchwork of authorization systems that are difficult to maintain, prone to security gaps, and frustrating for both administrators and end users.
Introducing IOMETE's Resource Access Management System
IOMETE's RAS represents a fundamental reimagining of how authorization should work in a modern data platform. Built from the ground up with flexibility, performance, and simplicity in mind, RAS provides a unified authorization framework that seamlessly handles the diverse needs of a comprehensive data platform.
The Hierarchical Bundle Architecture
At the heart of IOMETE's RAS is a sophisticated three-tiered bundle hierarchy that mirrors how organizations naturally structure their data operations:
- Platform Bundles: The top-level organizational unit that provides platform-wide governance. Platform bundles contain high-level policies and can include multiple domains, making them ideal for enterprise-wide access control.
- Domain Bundles: Mid-level organizational units that represent business domains, departments, or major project areas. Domain bundles inherit from platform bundles while adding domain-specific policies for compute resources, Jupyter environments, Spark jobs, and secrets management.
- Resource Bundles: The most granular level, containing specific assets like individual compute instances, Spark jobs, worksheets, and secrets. Resource bundles provide fine-grained access control while inheriting broader policies from their parent domain and platform bundles.
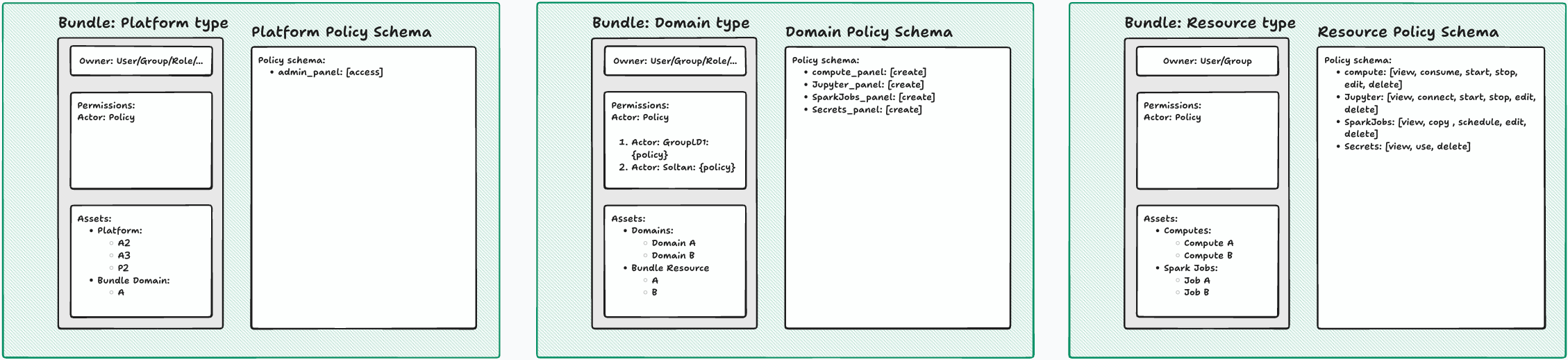

This hierarchical approach provides several key advantages:
- Organizational Alignment: The three-tier structure naturally reflects how enterprises organize their data teams and projects, making access management intuitive for administrators and users alike.
- Policy Inheritance: Lower-level bundles inherit permissions from their parents, reducing administrative overhead while maintaining the ability to add specific restrictions or permissions as needed.
- Scalable Governance: Platform administrators can set organization-wide policies that automatically apply across all domains and resources, while still allowing domain-specific customization.
- Performance Optimization: Authorization decisions can be made efficiently by traversing the hierarchy only as far as necessary, with each bundle storing its complete policy as a JSON document for fast local evaluation.
How Resource Access Management Works in IOMETE
Let's walk through the complete lifecycle of resource access management in IOMETE, from bundle creation to access enforcement.
1. Bundle Creation and Resource Organization
The process begins when users need to organize their resources. In IOMETE, this happens naturally as part of the platform workflow:
- User-Driven Organization: Users navigate to the compute create page and initiate the creation of new bundles to organize their resources logically
- Flexible Grouping: Resources can be grouped by project, team, environment, or any other logical structure that makes sense for the organization
- Automatic Policy Initialization: When a bundle is created, IOMETE automatically establishes the foundational authorization policy
2. Resource Registration and Policy Definition
Once a bundle exists, resources are registered within it and policies are defined:
- Dynamic Registration: As new compute instances, Spark jobs, or other resources are created, they're automatically associated with the appropriate bundle
- Policy Customization: Bundle owners can define detailed permissions, specifying who can read, write, execute, or manage resources within the bundle
- Group Integration: Policies can reference both individual users and groups, providing flexibility in how permissions are assigned
3. Real-Time Authorization Decisions
When users interact with platform resources, RAS provides real-time authorization through two primary mechanisms:
-
Resource-Based Authorization: Every time a user attempts to access a resource, the relevant service makes an
isAuthorizedAPI call to RAS. For example:- When a user clicks "Edit" on a compute instance, the Compute API queries RAS to verify edit permissions
- When attempting to copy a Spark job, the SparkJob API validates copy permissions through RAS
- Before accessing sensitive configuration data, the Secrets API confirms read permissions
-
Group-Based Authorization: For scenarios requiring group membership validation, RAS provides
isMemberOfAPI calls that integrate seamlessly with existing LDAP and identity provider systems.
4. Dynamic Access Control
IOMETE's RAS goes beyond simple yes/no authorization decisions to provide dynamic, context-aware access control:
- Resource Listing: Users see only the resources they have permissions to access, creating a personalized view of the platform
- Action Filtering: Available actions (edit, delete, share, etc.) are filtered based on the user's specific permissions for each resource
- Group Management: Users can view and manage their group memberships, understanding exactly what access they have and why
The Technical Excellence Behind RAS
IOMETE's RAS achieves its effectiveness through several key technical innovations:
Pluggable Architecture
The system is designed with extensibility as a core principle. New resource types can be added to the platform without requiring changes to the authorization engine. This pluggable architecture means that as IOMETE evolves and adds new capabilities, the authorization system seamlessly grows with it.
Performance-Optimized Design
Authorization decisions happen in real-time, often multiple times per user request. RAS is optimized for performance through:
- Local Decision Making: Policies are stored directly with bundles, eliminating network round-trips for authorization decisions
- Efficient Caching: Frequently accessed authorization decisions are cached to reduce latency
- Optimized Data Structures: The JSON policy format is designed for fast parsing and evaluation
Comprehensive Audit Trail
Every authorization decision is logged, providing a complete audit trail for compliance and security analysis. This includes not just successful access grants, but also denied requests, helping organizations understand both legitimate usage patterns and potential security threats.
Real-World Impact: RAS in Action
Cross-Team Project Collaboration
Let's examine how IOMETE's RAS handles a common enterprise scenario: cross-team collaboration on a time-sensitive project.
The Challenge: Carol, a Data Engineer from Marketing Analytics, needs to lead a campaign analysis project that requires collaboration with Emma from Sales Analytics and monitoring access for Frank, a Marketing Manager. Traditional authorization systems would require IT intervention, complex permission matrices, and often result in either over-permissioning (security risk) or under-permissioning (productivity loss).
The IOMETE RAS Solution:
-
Step 1: Self-Service Project Setup
Carol creates a project-specific bundle called "Campaign-Analysis-Project" directly through the platform interface. She becomes the bundle owner with full control over project resources and access policies. -
Step 2: Resource Creation with Automatic Policy Inheritance
When Carol creates the "campaign-data-processor" compute cluster, she simply selects her project bundle during the creation process. The compute resource automatically inherits the bundle's permission structure - no separate authorization configuration required. -
Step 3: Granular Cross-Team Permissions
Carol uses the bundle management interface to grant specific access levels:- Emma (Sales Analytics): Execute permissions for running analysis jobs, but not cluster management
- Frank (Marketing Manager): View-only access for monitoring progress and logs
- Herself: Full ownership and management capabilities
-
Step 4: Dynamic Project Scaling
As the project evolves, Carol adds a second compute cluster for machine learning models. Emma and Frank automatically receive the same access levels to the new resource - the bundle policy ensures consistent permissions across all project assets.
The Technical Beauty: JSON Policy in Action
Behind this seamless user experience, IOMETE's RAS manages access through elegant JSON policies:
{
"bundleId": "campaign-analysis-project",
"owner": {
"id": "carol",
"type": "user"
},
"assets": {
"compute": ["campaign-data-processor", "campaign-ml-models"],
"spark_job": ["analysis-job", "model-training-job"]
},
"permissions": {
"compute": {
"users": {
"emma": ["consume", "execute"],
"frank": ["view"]
}
}
}
}
This single policy document enables:
- Resource Grouping: All project assets are logically organized and managed together
- Permission Inheritance: New resources automatically get appropriate access policies
- Fine-Grained Control: Different users get precisely the access they need
- Audit Trail: Every access decision is traceable to specific policy rules
Authorization in Action: When Emma clicks "Connect" on the campaign-data-processor cluster, IOMETE's RAS immediately checks this policy document. The system sees that Emma has ["consume", "execute"] permissions for compute resources in this bundle, so it grants her access to connect and run jobs. However, when she tries to modify cluster settings, the system denies access since "manage" isn't in her permission list.
Dynamic Resource Discovery: When Carol adds the new "campaign-ml-models" compute cluster to this bundle, Emma automatically gains the same access level without any additional configuration. The policy applies to all compute assets within the bundle, making resource management seamless.
Granular Control: Frank, with only ["view"] permissions, can see cluster status and monitor job execution in real-time, but cannot connect to run his own analysis or modify any settings. This precise control ensures everyone gets exactly the access they need for their role in the project.
The Enterprise Impact
This scenario demonstrates several critical advantages of IOMETE's approach:
- Zero IT Bottlenecks: Carol set up cross-team collaboration in minutes, not days or weeks of IT ticket processing.
- Security by Default: Each collaborator gets exactly the access they need - no more, no less. Frank can monitor project progress but cannot accidentally modify critical compute resources.
- Scalability Without Complexity: Adding new resources to the project maintains consistent access policies without requiring additional configuration.
- Clear Accountability: Bundle ownership provides clear lines of responsibility while enabling flexible collaboration patterns.
- Project Lifecycle Management: When the campaign analysis concludes, Carol can easily decommission the entire project bundle, automatically cleaning up all associated permissions and resources.
Conclusion
In an era where data platforms are becoming increasingly complex and critical to business operations, having a robust, flexible, and intelligent authorization system is no longer optional – it's essential. IOMETE's Resource Access Management system provides the foundation for secure, scalable, and user-friendly access control that grows with your organization's needs.
By combining the logical simplicity of bundle-based organization with the technical sophistication of pluggable authorization engines, RAS delivers on the promise of unified access management without sacrificing performance or flexibility. For organizations looking to balance security with productivity in their data platforms, RAS provides the roadmap for success.
The future of data platform security isn't about building higher walls – it's about building smarter gates. IOMETE's RAS represents that intelligence in action, ensuring that the right people have access to the right resources at the right time, every time.